Enable ssl
sudo a2enmod ssl
Create new directory for the self signed certificate
sudo mkdir /etc/apache2/ssl
Create the self signed certificate and the server key that protects it, and placing both of them into the new directory
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/apache2/ssl/owncloud.key -out /etc/apache2/ssl/owncloud.crt
Now we setup the certificate
sudo nano /etc/apache2/sites-available/default-ssl.conf
The lines that need changing are the following
ServerName 192.168.1.11:443
SSLEngine on
SSLCertificateFile /etc/apache2/ssl/owncloud.crt
SSLCertificateKeyFile /etc/apache2/ssl/owncloud.key
Activate the new vhost
sudo a2ensite default-ssl
Restart apache
sudo service apache2 restart...
Category Archives: News
Hardening your Apache and PHP on Ubuntu 9.04 Server
You have installed LAMP and OpenSSH on your Ubuntu 9.04 Server. The first thing to do is to harden it in order to avoid some kind of attacks.
You can do the following steps in front of your Ubuntu 9.04 Server or remote access it via OpenSSH.
For OpenSSH, your Ubuntu 9.04 Server is at 192.168.0.10 :
ssh 192.168.0.10 -l nikesh
Step 1 :
The avoid someone to list your files on your Apache directory, you should do the following step.
sudo nano /etc/apache2/sites-available/default
Add a minus "-" in the front of "Indexes" and it will looking like this :
" :
RewriteEngine On
RewriteCond %{REQUEST_METHOD} ^(TRACE|TRACK)
RewriteRule .* - [F]
Step 3 :
To avoid HTTP DoS,...
How to Protect your Server Against the Shellshock Bash Vulnerability
On September 24, 2014, a GNU Bash vulnerability, referred to as Shellshock or the "Bash Bug", was disclosed. In short, the vulnerability allows remote attackers to execute arbitrary code given certain conditions, by passing strings of code following environment variable assignments. Because of Bash's ubiquitous status amongst Linux, BSD, and Mac OS X distributions, many computers are vulnerable to Shellshock; all unpatched Bash versions between 1.14 through 4.3 (i.e. all releases until now) are at risk.
The Shellshock vulnerability can be exploited on systems that are running Services or applications that allow unauthorized remote users to assign Bash environment variables. Examples of exploitable systems include the following:
- Apache HTTP Servers that use CGI scripts (via
mod_cgiandmod_cgid) that are written in Bash or launch to Bash subshells - Certain DHCP clients
- OpenSSH servers that use the
ForceCommandcapability - Various network-exposed services that use Bash
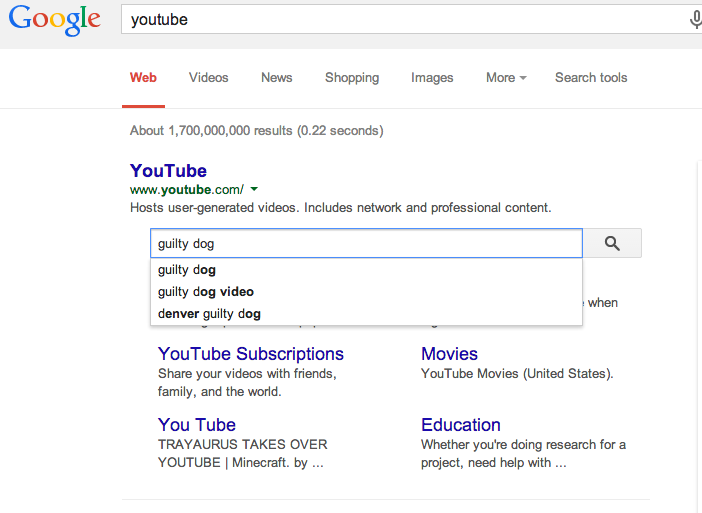
Google Launches Improved Sitelinks Search Box
Google has introduced a new sitelink feature where it will show a site search box above the sitelinks for a website in the search results.
The new change, in addition to the search box getting a prominent spot just under the site description, also takes advantage of auto-complete when people type something into the search box.
The new search box is available for both desktop and mobile searches. Here it is for desktop:
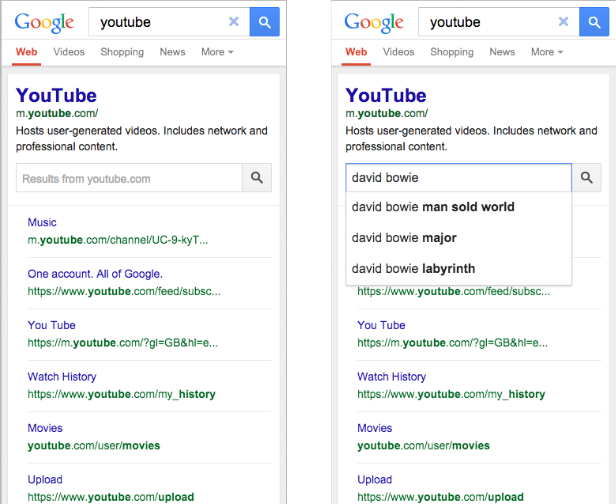
 Here is the mobile version of the new search box.
Here is the mobile version of the new search box.
 Google provides documentation so webmasters can enable this so any searches done within the sitelinks search box will direct people right to the results page on your site. You need to have a working search engine on your site, however...
Google provides documentation so webmasters can enable this so any searches done within the sitelinks search box will direct people right to the results page on your site. You need to have a working search engine on your site, however...
 Here is the mobile version of the new search box.
Here is the mobile version of the new search box.
 Google provides documentation so webmasters can enable this so any searches done within the sitelinks search box will direct people right to the results page on your site. You need to have a working search engine on your site, however...
Google provides documentation so webmasters can enable this so any searches done within the sitelinks search box will direct people right to the results page on your site. You need to have a working search engine on your site, however...
Converting WAV files
Converting WAV files
If you have a wav file (in what format?) you can convert it using the sox program. - Raw linear, signed 16 bit, mono, 8000 Hz (.slin)sox file.wav -t raw -r 8000 -c 1 -w -s file.slin- Raw mu-law, mono, 8000 Hz (.mulaw or .u)
sox file.wav -t raw -r 8000 -c 1 -b 8 -U file.mulaw- Raw A-law, mono, 8000 Hz (.alaw or .A)
sox file.wav -t raw -r 8000 -c 1 -b 8 -A file.alaw- Raw GSM, mono, 8000 Hz (.gsm)
sox file.wav -t raw -r 8000 -c 1 -b 8 -g file.gsm
(not all versions of sox support this conversion)
- SUN/SGI audio/basic file, mono 8000 Hz (.au) containing:
- Signed linear ...
VPN Installer for CentOS 6 Installation
To get started with your own secure VPN, simply execute the following commands at your servers command-line:
yum install -y git
cd /opt && git clone git://github.com/drewsymo/VPN.git
cd VPN && bash vpn-setup-vanilla.sh
If you’re on Linode, you can simply rebuild your instance with the PPTP VPN Installer StackScript.
Note: OpenVZ users, currently one of the iptables rules used in this script is not virtualised in OpenVZ (masquerade). This means you will need to run this line of code once you have finished installing the CentOS PPTP VPN script for it to work:
iptables -t nat -A POSTROUTING -j SNAT --to-source x.x.x.x
Where x.x.x.x is your venet0 IP address
In addition to this, you will also need OpenVZ kernel 2.6.32
How do I connect to my VPN?
You can now connect to your VPN using your servers IP as the hostname (this depends on your VPN...
